Running Secure Power Automate Flows
Power Automate Best Practices
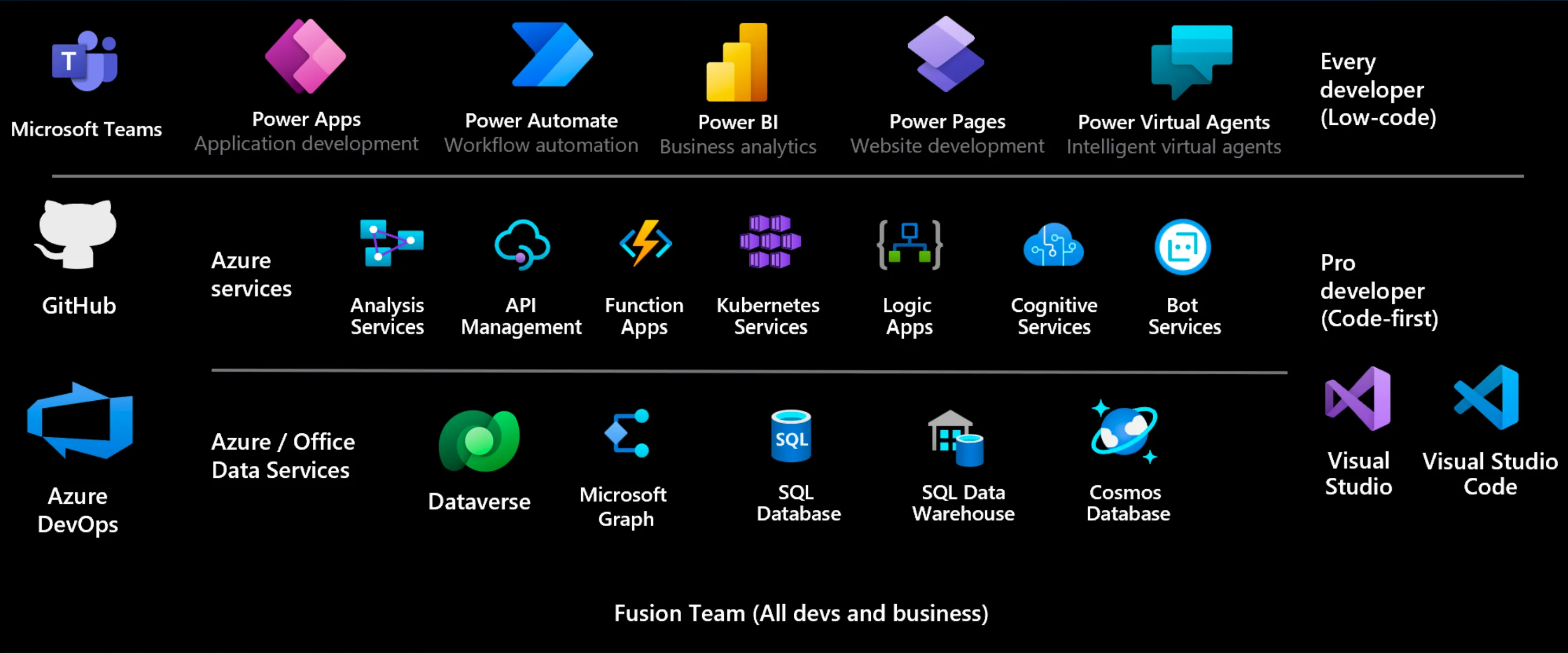
By touching the Power Platforn, you will need to have a deeper understanding on the underlying services and tools. There is a whole set of products that bring up to extend the OOTB capabilites of the Power Platform.
Data requests can be sent through several HTTP(s) requests (connectors).
Connecting to API’s to connect services (Outgoing HTTP requests)
Warning
Always store passwords / credentials in Azure KeyVault.◊
Possiblitites to secure a HTTP connector sending HTTP Requests (on most connectors) in Power Automate:
- Client Certificate Auth
- Default Microsoft Entra ID (preatuhorized)
- Service Principals (Entra ID OAuth)
- Managed Identity (does not work with SharePoint)
- Basic Auth (with / without MFA)
Note
There is no option to send an HTTP request to SharePoint other than with a dedicated service account (the reason for this lies in the underlying architecture: SPO stores its data in an SQL database which needs dedicated user credentials to proceed the data request).
Security possiblilies to secure a Custom Connector in Power Automate:
- Anonymous
- Basic
- API Key (Header + Query)
- OAuth 2.0
- “Toggle” aka Multiple authentications on a custom connector
—> you will need the Microsoft Power Platform Connectors CLI; see https://learn.microsoft.com/en-us/connectors/custom-connectors/multi-auth for reference
Incoming HTTP requests
When using the “When a HTTP request is triggered” connector, make sure you secure it via the Azure API Management.
Summary
For outgoing requests:
- use service principals whenever possible
- use built-in capabilities to secure data
- use service accounts for Saas services
- use secure inputs and outputs in Power Automate
For incoming requests:
- always consider using Azure API Managemnet to make the real HTTP webhook url transparent to the caller
- use Azure Key Vault to store secrets